As we all know, installation packages created by the native NSIS can be easily extracted by 7z. The installed files, NSIS scripts, plugins, and even UI resource packages can be easily viewed. Although the readability of the extracted script may not be very strong, it does not hinder the analysis of the logical installation process. In fact, some scripts can be copied and reused directly!
The first example on our website, because no special treatment has been done in this regard, can also be extracted in this way.
Just imagine, you or your company's team spent a lot of time carefully designing the installation interface, only to be easily extracted by others and used elsewhere. Doesn't it feel painful?
Developers who work overtime and overnight to add control logic to the installation package intended to limit the installation behavior may find it disappointing when the script logic is completely exposed to others after extraction.
Here is the process of extracting a typical NSIS installation package:
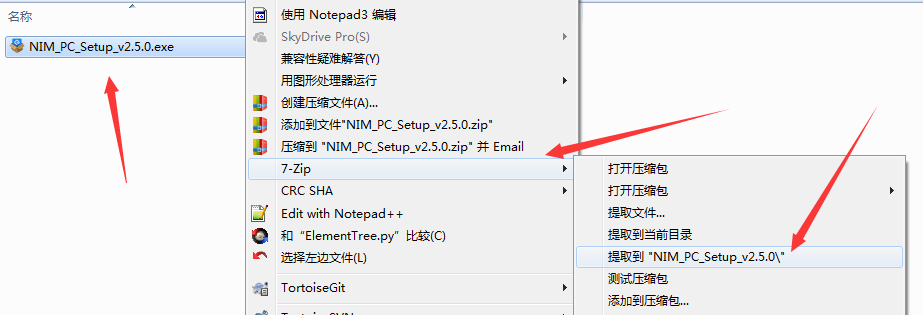
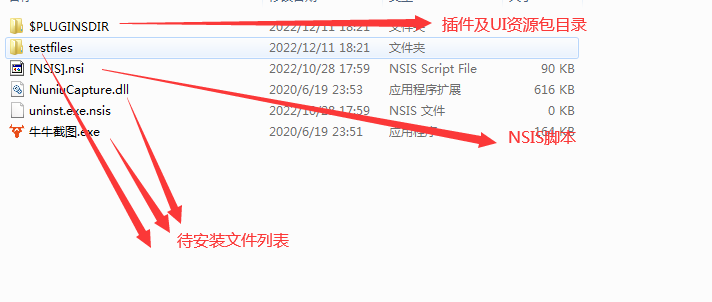
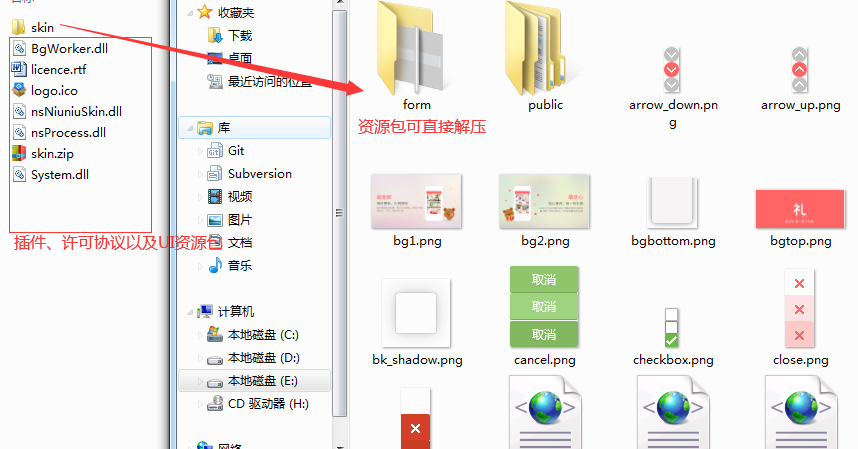
It can be seen that plugins and NSIS scripts are both extracted, and there are the following issues overall:
I was troubled by this for a long time, but fortunately, I have now found a solution. In fact, there are two issues we need to address:
In the nsNiuniuSkin installation package packaging solution, we have adjusted the compression method of NSIS to avoid extraction by 7z. At the same time, we have applied strong encryption to the UI resource package to ensure the overall security of the installation package resources.
Let's see how our new version solves these problems and check if the installation package produced by the new version is really secure!
This is relatively simple. We applied an enhanced version of the NSIS script compiler, which can adjust the compression method of the compiled exe, making it unrecognizable by 7z. Naturally, it cannot be extracted. Taking the installation package of our nsNiuniuSkin interface online design engine as an example, let's see if it can really prevent extraction:
Why mention this separately? The reason is that when the NSIS installation package program starts, it will automatically create a temporary directory under the system's %tmp% directory, which contains the plugins used by the installation package. At the same time, in the nsNiuniuSkin installation package solution, the license agreement and UI resource package used during the installation process will also be stored in this temporary directory.
In this way, if you go to the %tmp% directory after opening the installation package program, you can see the plugins and resources that the installation package depends on.
Here is the file list under the temporary directory when the installation package of our nsNiuniuSkin interface online design engine starts:
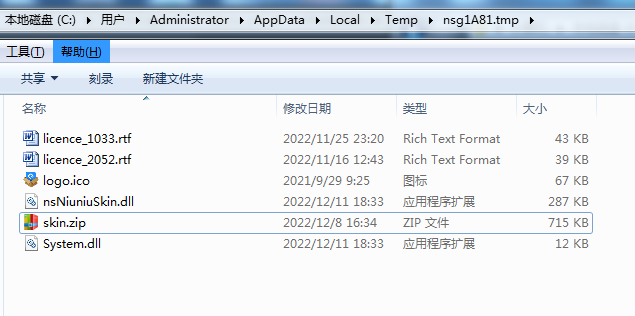
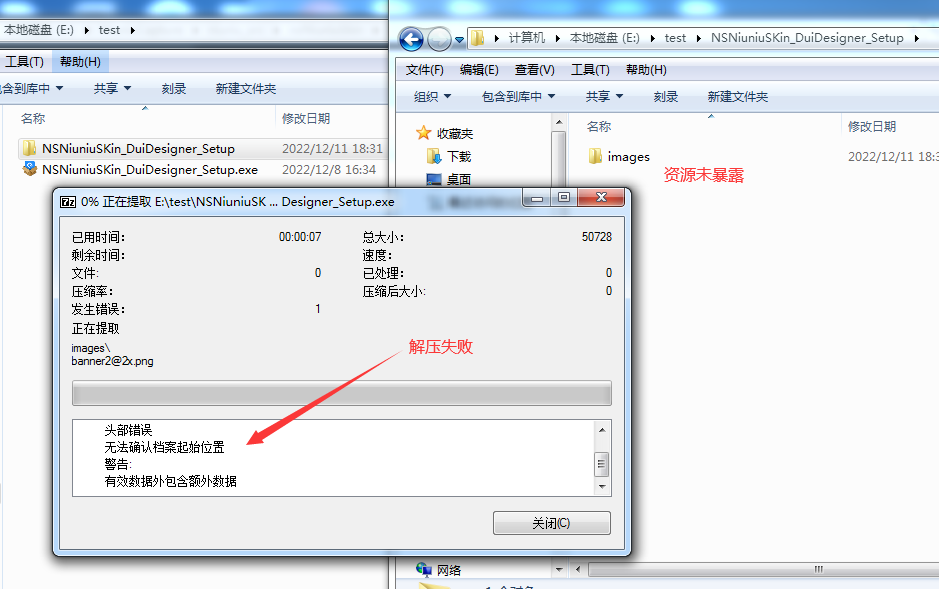
You can see a file named "skin.zip," which is used to store the resource package containing installation package images and interface configuration scripts. You may ask, isn't this already exposed?
Don't worry, try to unzip it, and you will find that it cannot be extracted:
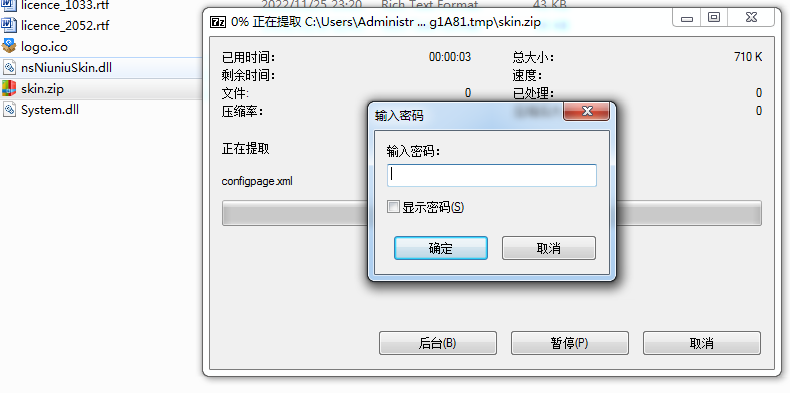
High-strength password protection:
This is because when we package it, we encrypt the generated zip package with a password. At the same time, when the installation package starts, it decrypts the resource package in memory and then extracts the resources for rendering and display. Moreover, we use a password that is randomly generated as a uuid each time we package it. On the premise of the security of the NSIS script itself, frankly, I don't know how to decrypt the resource package of this installation package.
It's a bit embarrassing to say that I can't extract my own package. However, since we pursue security, I think it should be like this!
The encryption logic will not have any impact on the running performance of the installation package. You can also download and experience it directly. If you are interested, you can try to extract it and give me feedback on any shortcomings so that I can improve it!
http://www.ggniu.com/download/NSNiuniuSKin_DuiDesigner_Setup.exe
In the making and application of installation packages, functionality and aesthetics are of course the top priorities. However, security is also an important point that cannot be ignored. If you happen to have security requirements for installation packages and happen to see this article, our story begins!
In the installation process of installation packages, exquisite UIs often leave a deep impression on customers, reflecting the dedication and care of software service providers in user experience! We hope that our efforts will make installation package creation a bit easier and more enjoyable!
May there be no difficult installation packages in the world!